CVE-2021-34527 (associated with CVE-2021-1675, also known as “PrintNightmare”) is a Critical Vulnerability in the Windows Print Spooler that requires immediate action.
- 2021-07-09 – update with link to Microsoft clarification and third-party flow chart
- 2021-07-06 – update with Microsoft announcement of patch
- 2021-07-02 – update with new CVE and response from Microsoft. add link to third-party graphic.
- 2021-07-01 – add links for mitigation and detection. add links to technical writeup and CISA alert.
Risk: Critical
Likelihood of exploitation: High
Exploit Code: Publicly available
Exploitation in wild: Yes
Description of vulnerability: The print spooler service is vulnerable to remote code execution that leverages a compromised user account, either domain-joined or local account, to take full control of a system as the NT SYSTEM user. Proof-of-concept (PoC) code has been made publicly available for this new vulnerability leaving every Windows system at extreme risk. An adversary exploiting this vulnerability can leverage a domain-joined account, regardless of permissions, to take full control as NT SYSTEM on any domain-joined Windows system. This includes servers and Domain Controllers. An adversary exploiting this vulnerability can also leverage a local account to take full control as NT SYSTEM on any Windows system that the local account is valid. See also: official Microsoft description of vulnerability.
Remediation: See official Microsoft guidance and clarified guidance.The patch and accompanying configuration changes may not provide complete protection. We advise consulting this flow chart provided by security researcher Will Dormann. Please note that he most effective mitigation is to disable the print spooler service on all Windows devices. Information Security’s recommendation is to prioritize Domain Controllers, then critical servers, then assess where the print spooler service is needed and disable it where it is unnecessary. For everything else, which may include many workstations, you will need to weigh the risks of temporarily lost functionality against possible system compromise. Although there are many ways to disable a service on a Windows system, we have provided two easy options that any individual user can do on their own. For IT Administrators, we recommend using professional judgement on how to disable. One option for administrators is to leverage GPO to make this change.
Options for Disabling Print Spooler Service
Option 1: Disabling the print spooler Service via CMD:
Do the following:
- Press Windows key + R to invoke the Run dialog.
- In the Run dialog box, type
cmdand then press CTRL + SHIFT + ENTER to open Command Prompt in admin/elevated mode. - In the command prompt window, type the commands below and hit Enter to disable and stop the Print Spooler service.
sc config "Spooler" start=disabled sc stop "Spooler"
Option 2: Disabling the print spooler Service via Services MMC:
Do the following:
- Press Windows key + R to invoke the Run dialog.
- In the Run dialog box, type
services.mscand hit Enter to open Services. - In the Services window, scroll and locate the Print Spooler service.
- Double-click on the entry to open its properties window.
- In the properties window, on the General tab, move to the first section titled Startup type section and select the Disabled option from the drop-down menu in order to disable the service upon System bootup.
- In the properties window, on the General tab, move to the second section titled Service status section and click the Stop button in order to disable the service.
- Click ‘Apply’ to apply the changes.
- Click ‘Ok’ to finish.
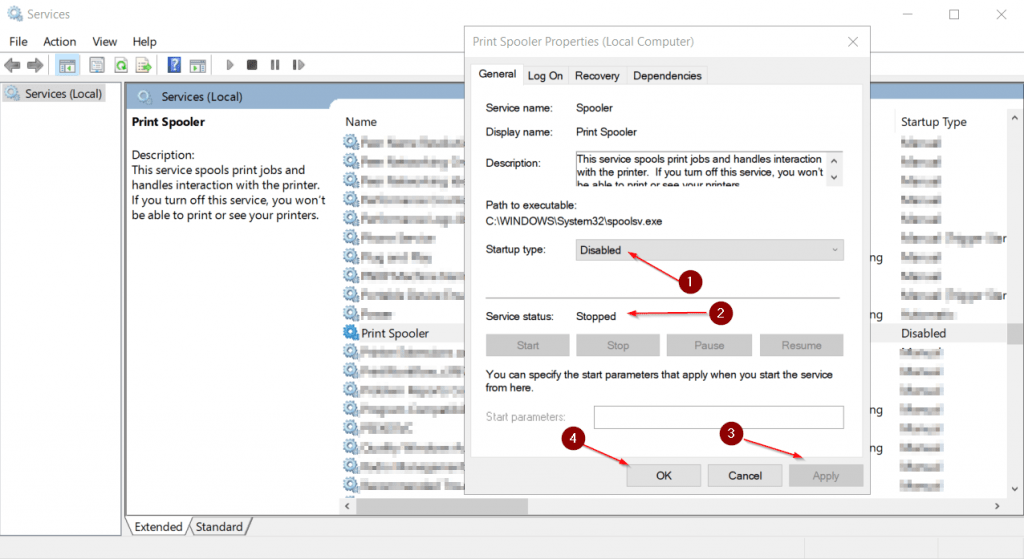
Demonstration of Print Spooler Properties Dialog
Alternative mitigation options
Please note that due to the lack of official guidance from Microsoft many IT professionals are posting recommendations for mitigations. We are linking to some that originate from high quality sources for your consideration, but links do not indicate endorsement or recommendation to implement. Use your professional judgement and take reasonable precautions such as testing in non-production environments. If you do identify useful mitigations lease share your results with the University IT community.
- https://blog.truesec.com/2021/06/30/fix-for-printnightmare-cve-2021-1675-exploit-to-keep-your-print-servers-running-while-a-patch-is-not-available/
Recommendations for Detection
- Install CrowdStrike Falcon
- Configure centralized event logging, ideally with the Microsoft-Windows-PrintService/Operational event log (disabled by default) and monitoring for event ID 316
More Details:
- https://twitter.com/hackerfantastic/status/1410100394492112898?s=20 – A respected security researcher proving that the patch is ineffective and the only mitigation is to disable print spooler service.
- https://twitter.com/gentilkiwi/status/1410246348784422916?s=20 – The author of mimikatz, one of the most widely used Windows credential stealing programs, also demonstrating the patch is ineffective and how serious this risk is.
- https://twitter.com/0gtweet/status/1410150462842544130?s=20 – This is a respected blue team security researcher who is sharing some tips on how to disable the print spooler service in bulk.
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1675 – As mentioned in the description on this page, it’s unclear whether this new vulnerability is a variant of CVE-2021-1675 or a new 0day exploit.
- https://doublepulsar.com/zero-day-for-every-supported-windows-os-version-in-the-wild-printnightmare-b3fdb82f840c – Provides a technical description of how the vulnerability can be exploited.
- https://us-cert.cisa.gov/ncas/current-activity/2021/06/30/printnightmare-critical-windows-print-spooler-vulnerability – CyberSecurity & Infrastructure Agency (CISA) Vulnerability notice
Please direct questions as appropriate to security@uchicago.edu or 773-702-2378.