Ransomware attacks are one of the most serious cybersecurity threats we face at the University of Chicago. Ransomware is a type of malicious software that steals user data, disables the user system, and then demands payment from the victim in order to re-enable system access and to prevent disclosure of private data on the internet. Schools such as the University of California San Francisco and Michigan State University suffered ransomware attacks this past year that cost those institutions more than $1 million each and caused weeks of disruption to researchers and staff.
With more ransomware attacks occurring every day, the threat has grown so severe that the U.S. Department of Justice recently announced ransomware will be investigated using techniques normally reserved for countering terrorist activity.
How do attacks work
Cyber criminals use several methods to carry out ransomware attacks. Common tactics include:
- Remote Access Services: Services such as Remote Desktop Protocol (RDP), Virtual Network Computing (VNC), and others allow users to connect and control a device from a remote online location. If the service is misconfigured or accessible using a weak or compromised password, a cyber criminal can take control of the system and initiate an attack.
- Phishing Emails: A phishing email is a legitimate-looking email that appears to come from a well-known and trustworthy organization or website but is really an attempt to gather personal and financial information from a recipient. The email may contain a link or an attachment that will initiate an attack once opened or may lead the recipient to a fraudulent website that harvests their password.
- Software Vulnerabilities: Cyber criminals take advantage of existing security gaps or vulnerabilities from well-known software and hardware in popular technology manufacturers to gain control of a device and deploy ransomware.
Steps to take if you suspect an attack
The University has implemented numerous tools to protect users from threats such as ransomware, but no security tool can provide perfect protection from all threats. Signs of an attack include a message appearing on your computer that demands payment or the sudden inability to access files. If you suspect your computer might be infected with ransomware, take the following actions:
- Immediately disconnect and turn off your computer to reduce the ransomware’s ability to spread further.
- Contact the Information Security office for assistance by calling 773.702.2378. This hotline is staffed 24×7, 365 days a year.
- Refer to the images below for examples of ransomware messages.
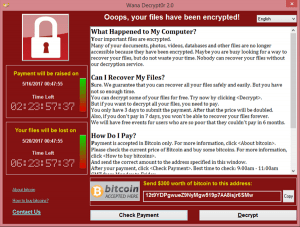
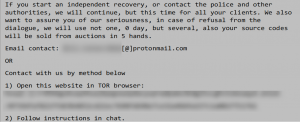
It is important to contact Information Security as soon as you believe a ransomware infection may have occurred. By notifying Information Security, the University can coordinate across technical teams to isolate infected areas of the network and activate additional resources to respond to the attack.
Information Security will coordinate with your local IT support after you contact us. Our goal is to help restore your computer as quickly as possible and to minimize the potential for damage to other parts of the University.
Protect your devices and information
There are steps you can take to protect your computer and data. The University has made site licensed tools available for use on all computers used by faculty and staff for University business.
- Install modern antivirus software (CrowdStrike). By installing this software on your computers, you are much less likely to be infected with ransomware should you be targeted.
- Install end user backup software (Code42 CrashPlan). Having robust backups is one of the quickest and most reliable ways to recover your data from a ransomware attack.
- Both tools have been reviewed and endorsed by the Board of Computing Activities and Services (BCAS) for use on faculty as well as staff computers.
- Please talk with your local IT support for assistance obtaining these tools for your computer(s) if they are not already installed.
Additionally, ensure you are following basic information security best practices, like using strong passwords. For more guidance, visit the Information Security website. IT Services is also developing a campus-wide Security Awareness Training to inform the University community about security concerns and prevention methods.
If you have any questions or want to learn more, you can always contact the Information Security office at security@uchicago.edu.