Follow These Steps to Protect Yourself from Phishing
Chances are good that at some point you’ve received a suspicious email urging you to click on a link or open an attachment. This email was most likely an example of the cybercrime known as phishing. Phishing is when cybercriminals send malicious emails designed to trick people into falling for a scam. The intent is often to get users to reveal financial information, system credentials (i.e, CNetID and password), or other sensitive data.
Cybercriminals use phishing because it’s easy, cheap, and effective. Email addresses are easy to obtain, and emails are virtually free to send. With little effort and little cost, attackers can quickly gain access to valuable data. Those who fall for phishing scams may end up with malware infections (including ransomware), identity theft, and data loss.
Cybercriminals use three primary mechanisms within phishing emails to steal your information: malicious web links, malicious attachments, and fraudulent data-entry forms. For the latest phishing emails reported or identified by Information Security, visit https://security.uchicago.edu/phishing/latest/.
Here are 3 things you can do when you receive a phishing email:
Step 1: Report it
IT Services implemented a Report Phish button in supported versions of Outlook for Windows, Outlook for Mac, Outlook on the Web, and Gmail clients to improve email security and response. The purpose of this button is to give you a simple way to report to IT Services any suspected phishing scam emails that our email protection systems failed to block and were consequently delivered to your inbox. When using the Report Phish Button, Information Security will be provided all the relevant information found in the headers (read the Email Protection FAQ to learn more).
Check out this short video on how to locate and the Report Phish feature.
Or, you can forward the phishing email as an attachment to security@uchicago.edu (see KB00015304). Forwarding the email as an attachment will ensure proper formatting of the email headers so that Information Security can take the appropriate action to mitigate the risks associated with these emails.
Step 2: Delete it
After reporting a phishing email, delete it and spread the word to your colleagues. It is very likely that you were not the only one to receive that phishing email. Some departments will be targeted by cybercriminals primarily for financial gain. This is known as spearphishing. These types of phishing emails will not have a link, but will impersonate someone with status in your department or at the University to get you to respond. Do not act without verifying the sender.
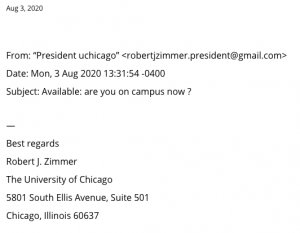
Below is an example of a spearphishing email reported and posted by Information Security for awareness in August 2020. Visit https://security.uchicago.edu/phishing/latest/ regularly to stay up to date on the latest email scams reported to Information Security.
3.) Contact us
Anyone can be tricked into falling for a phishing email. Given the right time and the right email message, anyone can overlook a phishing email. In the event that you do respond to a phishing email or entered your CNetID credentials into a fraudulent UChicago site, visit https://myaccount.uchicago.edu to change your password immediately. Contact Information Security via email or calling by (773)702-CERT(2378). We are here for you! There is so much we can learn from each other to keep the UChicago community safe online.
Do Your Part. #BeCyberSmart